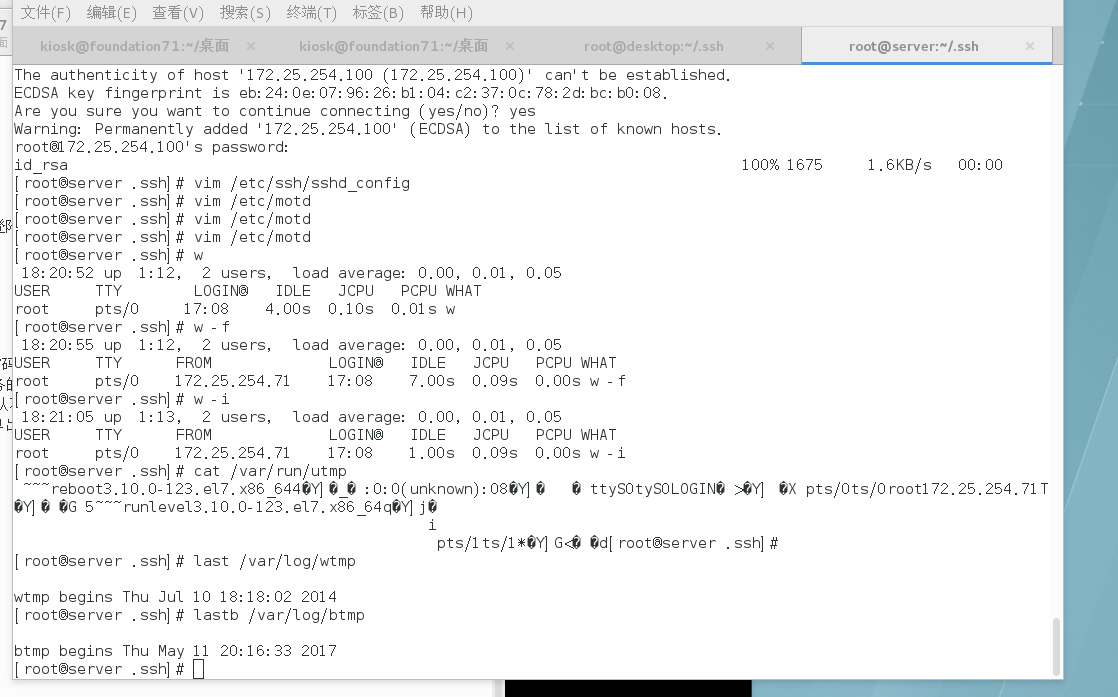
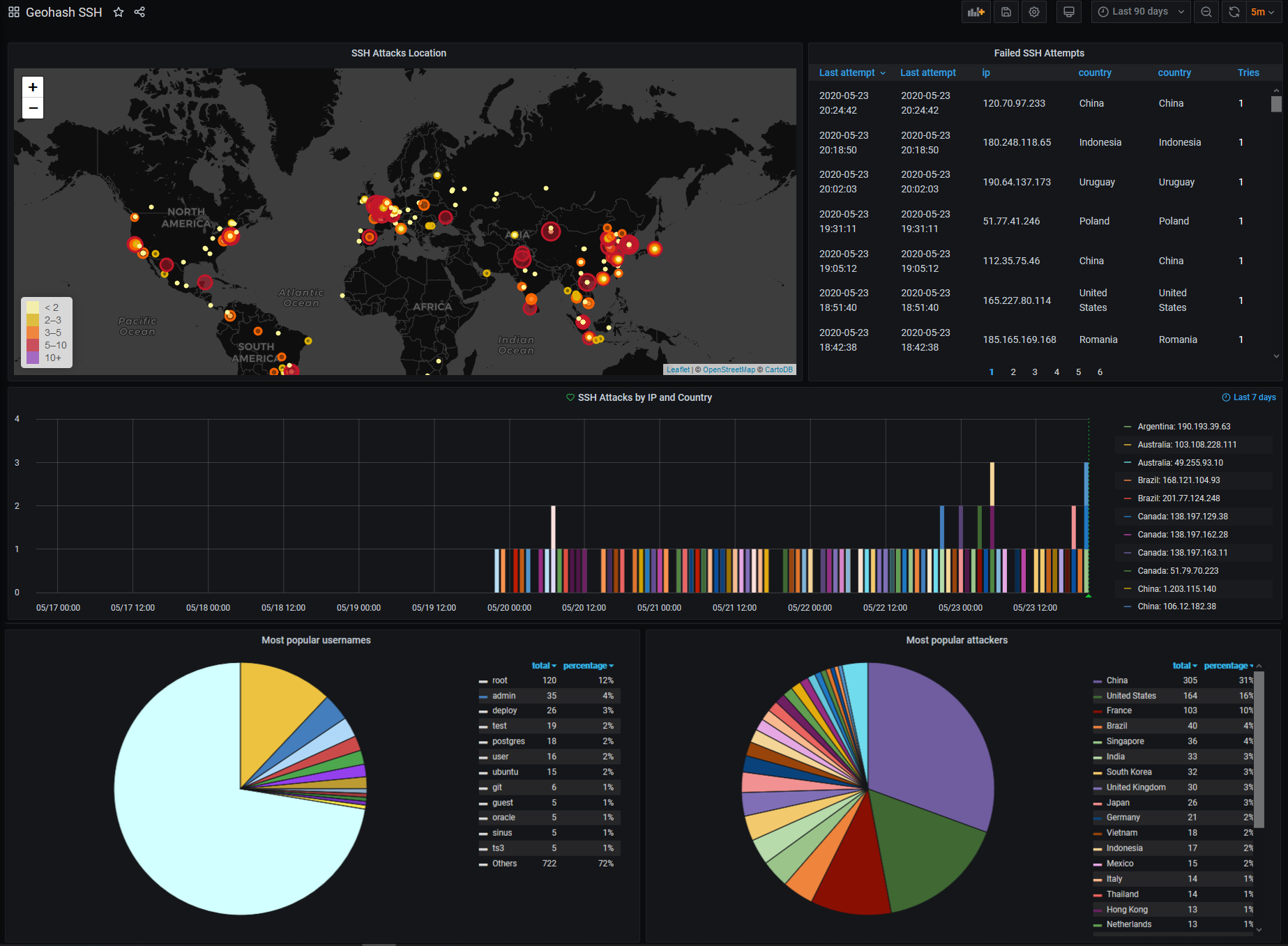
How to Monitor and Visualize Failed SSH Access Attempts to Amazon EC2 Linux Instances | AWS Security Blog

Is it possible to have 2 ports open on SSH with 2 different authentication schemes? - Unix & Linux Stack Exchange

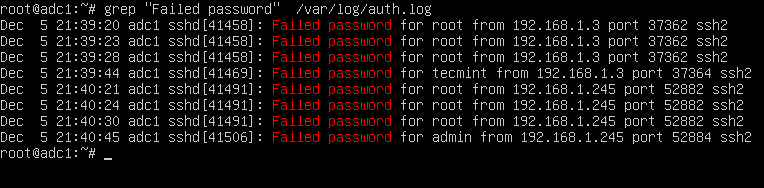
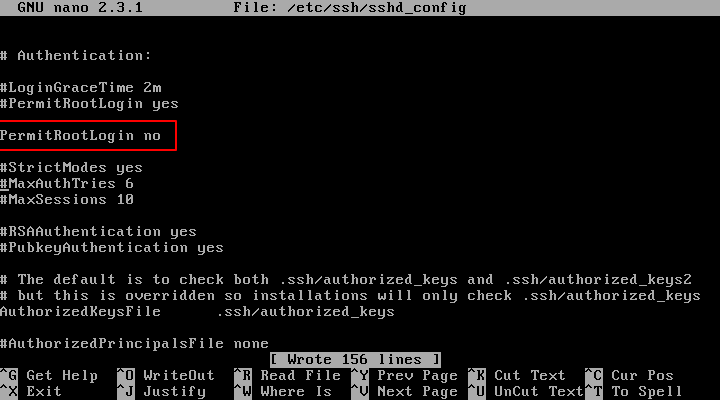
Yet another ssh brute force attack and how to protect against it with iptables and sshguard – The GNU of Life, the Universe and Everything